Healthy Technology Habits


Identity protection has never been a hotter topic, and it seems as if securing your identity is growing more challenging by the day. Hackers, phishers, and identity thieves continue to find new ways to cause security breaches and infiltrate people’s databases, email and financial accounts. You may be asking yourself: “What can I do to guard against identity theft? What does Yeske Buie do for me to guard against identity theft?” As we’ve said in this space before, one of the best defenses is a good offense and there are several habits that you can practice to keep your identity safe. We’ve listed a few of those habits below:
Review Your Accounts
- What can you do? Proactively review your accounts on a regular basis and make sure to read your Schwab and other financial account statements each month; once you’ve done so, shred them.
- What does Yeske Buie do? Yeske Buie monitors all deposits to and withdrawals from all of our Clients’ accounts daily.
Keep Your Passwords Safe
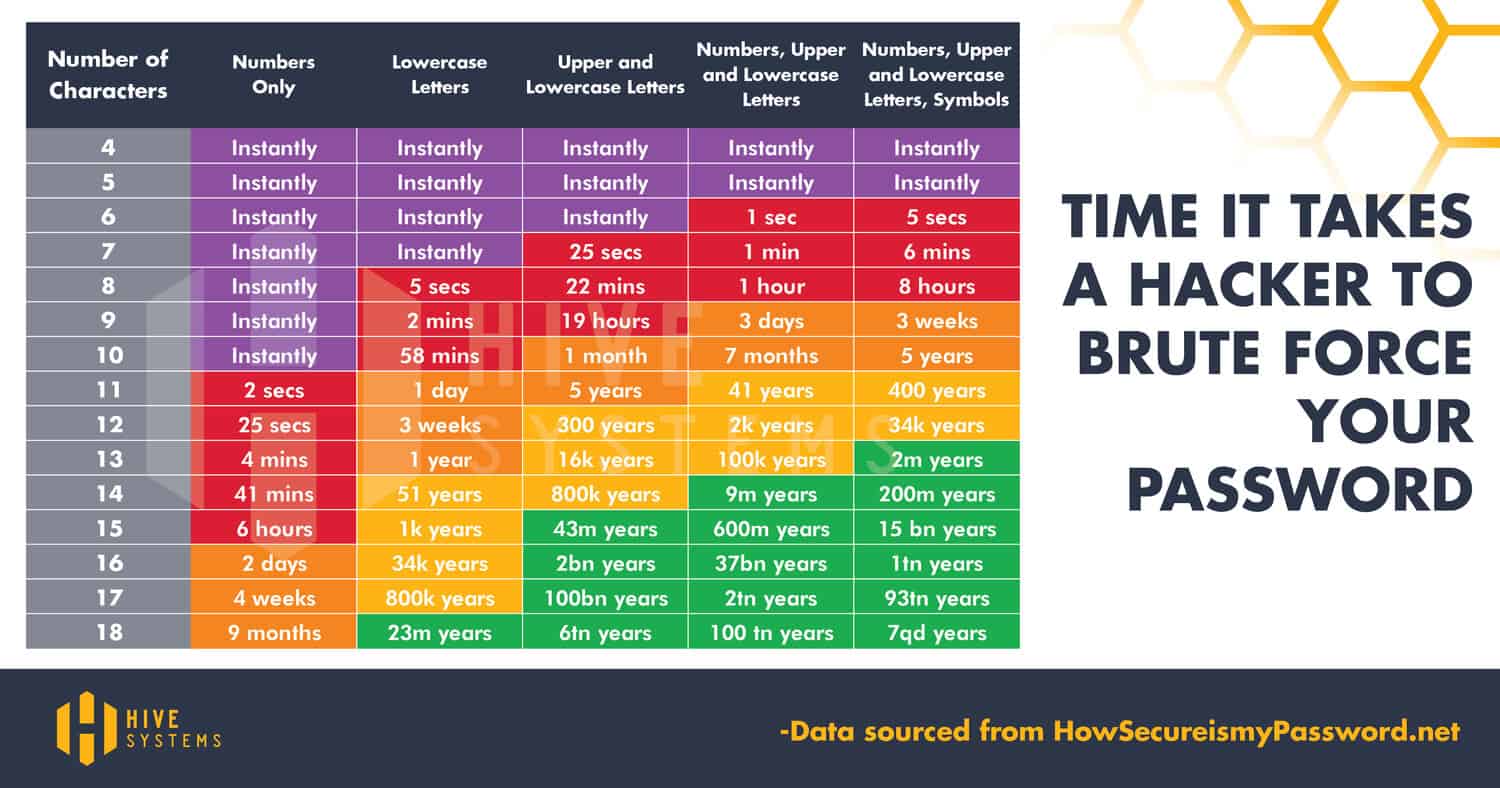
- What can you do? Keep your passwords in a safe location and structure them so that they’re not easy to guess. For tips, check out either of these sites – Tips for Strong, Secure Passwords or NIST Password Guidelines – and the infographic below that shows you the strength of a password based on the number and variety of characters.
- What does Yeske Buie do? All Yeske Buie team members are required to change their passwords periodically to ensure they remain strong and confidential. Additionally, we have policies regarding characters and sequences the password should and should not contain and we never reuse a password that we have used in the past.
Review Your Accounts
- What can you do? Proactively review your accounts on a regular basis and make sure to read your Schwab and other financial account statements each month; once you’ve done so, shred them.
- What does Yeske Buie do? Yeske Buie monitors all deposits to and withdrawals from all of our Clients’ accounts daily.
Keep Your Passwords Safe
- What can you do? Keep your passwords in a safe location and structure them so that they’re not easy to guess; for tips, check out either of these sites: Tips for Strong, Secure Passwords or NIST Password Guidelines.
- What does Yeske Buie do? All Yeske Buie team members are required to change their passwords periodically to ensure they remain strong and confidential. Additionally, we have policies regarding characters and sequences the password should and should not contain and we never reuse a password that we have used in the past.
Follow Healthy Email Protocols
- What can you do? Read all of your emails carefully, but make sure to be extra cautious before replying to requests that seem out of the ordinary in any way; for more information about preventing phishers from taking advantage of you, see this website: Phishing: Frequently Asked Questions. Also, you should never send personal information to anyone via email without ensuring it is securely protected: when sending information to Yeske Buie, we suggest you use one of these methods.
- What does Yeske Buie do? Yeske Buie always secures all personal information sent through email including paperwork, questionnaires, and requested statements using ShareFile. With ShareFile, all documents are sent via a secure link that expires after one week and uses a 256-bit encryption. If we receive any personal information that is not protected, we will save the information and then delete the email from our inbox as well as our deleted folder. We will recommend that the sender follow the same process.
Practice Responsible Use of Mobile Devices
- What can you do? Avoid unencrypted public wireless networks at all costs. If the Wi-Fi network does not require login information to access the network, that suggests that anyone, including phishers, can access them as well. We also suggest maintaining a strong password and changing the password at least every six months and reviewing the security settings on the phone to help ensure your data is secure.
- What does Yeske Buie do? When a Yeske Buie staff member has established access to the company’s systems enabling them to send and receive work-related email messages and conduct other company business on a mobile device, the devices are configured to be wiped clean of all personal information remotely if they are lost or stolen. We also keep these devices locked with a secure password and the device software is always kept current.
With the ocean of information available online, however, you shouldn’t hesitate to call in reinforcements to help safeguard your identity. We recommend using IdentityForce – each team member at YeBu is enrolled in their robust and comprehensive service, and you can subscribe with a discount through Yeske Buie by clicking here. Among a long list of other features, IdentityForce offers daily monitoring of all three of your credit reports, instant notifications when your personal information is being misused, and 24/7 fully-managed restoration services from their Certified Protection Experts.
If you find yourself to be the victim of identity theft or a security breach that could lead to your personal information being misused, we recommend navigating to the Federal Trade Commission’s site for a comprehensive list of what to do next. Additionally, we ask that you notify us immediately so we can ensure your accounts are secured. We place our entire team on high alert regarding all of your accounts as soon as we’re aware of fraudulent activity or receive suspicious communication and we make sure to alert Schwab of the breach immediately – any fraudulent transactions that Schwab processes are 100% reimbursed. It’s a good idea to have Schwab’s fraud investigation hotline – (877) 566-7984 – handy in the event you’re unable to reach us right away (ex. late in the evening or on a weekend).
While we don’t anticipate this problem fading away anytime soon, we’re confident that using a multifaceted strategy to combat identity theft is the best approach to securing your information. For more on what you can do to protect your identity, feel free to peruse the following articles we’ve written on the topic: